Call Today: 1-866-802-9405
Your company will be protected while you save time and money with TARA.
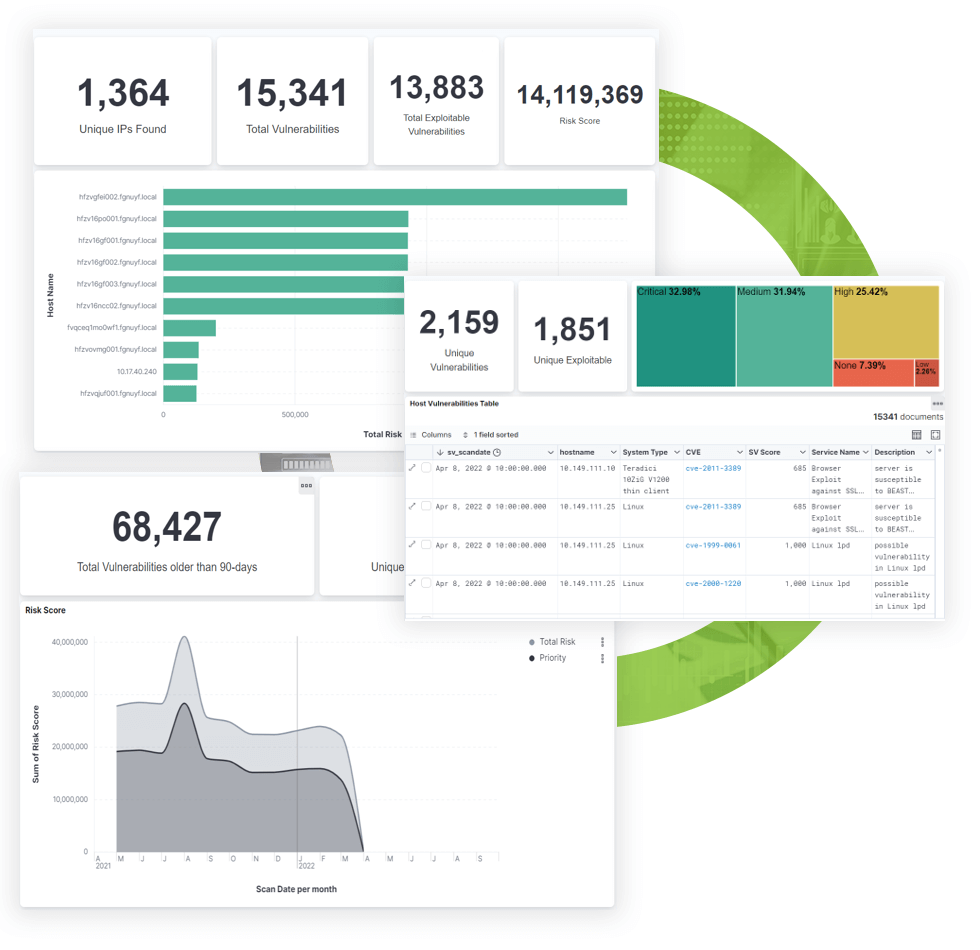
Security Vitals has developed the Compliance as a Service (CaaS) program to alleviate upfront investments in hardware, software and processes necessary to meet the CMMC requirements. The solution-driven approach is based on industry best practices to ensure ongoing compliance.